____________________
Do-It-Yourself
Remote eSIM Provisioning
__________
achelos enables players in the mobile ecosystem to fully harness the power of eSIM by hosting and operating services in their own preferred environment.
We offer a complete range of telco-grade solutions - from off-the-shelf, GSMA compliant Remote eSIM Provisioning to Profile Content Management and IoT Connectivity Orchestration.
As one of the leading software houses in this domain we can also rapidly develop customised extensions as well as fully bespoke systems to fulfil your specific requirements.
get in touch
The digital transformation of the plastic SIM into eSIM creates broad opportunities for innovative players.
With our solutions you take full control!
Benefit #1
commercial
INDEPENDENCE
Benefit #2
technical
AUTONOMY
Benefit #3
operational
SOVEREIGNTY
The early use of embedded chips in M2M devices created the need for remote profile provisioning, laying the foundation of eSIM technology.
eSIM then found its way into an ever growing amount of consumer devices, enabling a fully digital user experience.
For modern IoT devices, eSIM provides maximum efficiency, especially when implemented in the integrated iSIM form factor.
Whatever your use case, we provide the right component allowing you to build this crucial technology into your solution stack.
Use-Case #1
eSIM for CONSUMER
Telco Solution Providers can extend their existing portfolio with eSIM Management capabilities, while Mobile Operators, especially on a group level, can run the eSIM provisioning service in-network without 3rd party involvement.
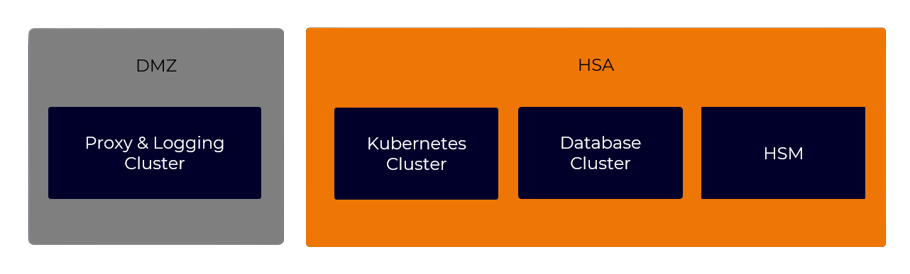
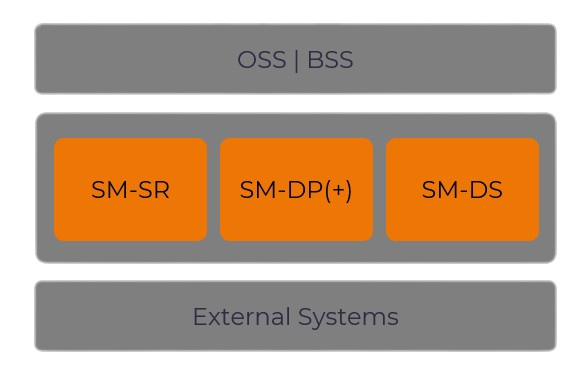
We have designed our SM-DP+ with integrated SM-DS component to be efficiently deployed into your preferred environment, whether private, public, or hybrid cloud.
Beside the standard ES2+ interface the extensive REST API of our solution allows easy integration with external systems and processes.
Use-Case #2
eSIM for IoT
The cost-sensitive nature of IoT makes eSIM management a valuable asset for MNOs, MVNOs, Service & Solution Providers as well as Chipset and Device manufacturers.
With SGP.32 a modern standard is becoming available based on SM-DP+ and SM-DS, introducing eIM (eSIM Remote IoT Manager) to support constraint devices in a flexible way. For management of devices compliant with the earlier M2M standard SGP.02 we offer SM-SR and SM-DP.
To facilitate complex procedures that go beyond GSMA's atomic operations we offer the IoT Connectivity Orchestrator. It acts as a middleware layer that effortlessly integrates external systems for event-triggered profile life cycle workflows.
Use-Case #3
eSIM for PRIVATE NETWORK
Enterprises and organisations are increasingly choosing to deploy private LTE and 5G networks, often coupled with the demand to have full control over data storage and processing.
For this particular application we offer an 'eSIM Management-in-a-box' solution with minimum footprint based on our telco-grade SM-DP+ solution. It guarantees the isolation of critical network access keys in security sensitive environments.